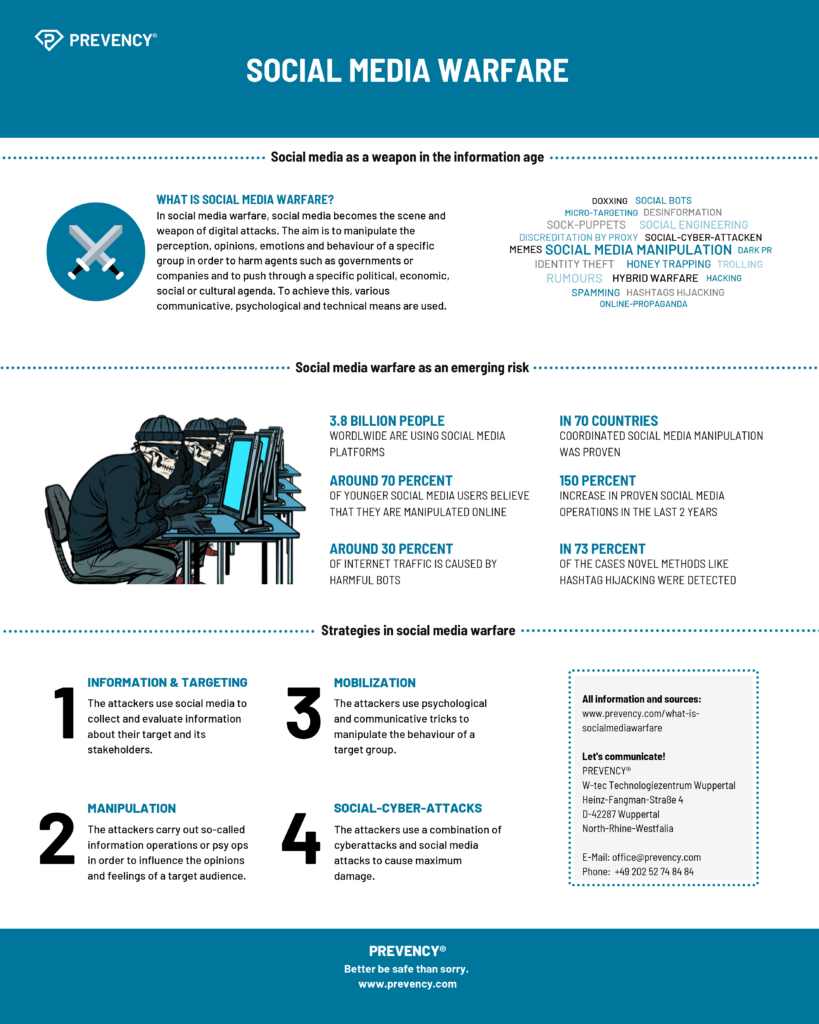
What is Social Media Warfare?
Social media as a weapon in the information age
It is impossible to imagine today’s information age without social media. Social media penetrates our everyday life, determines our private communication and companies or institutions present themselves in social web. The advantages are pretty obvious. Due to the way social media works, everyone – no matter if private person, politician or company – can achieve an enormous reach at low cost. Traditional gatekeepers like editorial offices are no longer needed, and everyone has the opportunity to distribute information with their own framing. This makes it easy to built up a digital reputation, increase sales or get better result in political election.
However, in addition to these positive effects, the way social media functions also poses numerous threat. Social media makes it increasingly easy to manipulate public opinion, defame companies and institutions or spread false and reputation-damaging content. Against this background, the Internet and especially social media can become a weapon and the scene of a virtual war. In this information war, actors fight to assert their own political, economic, social or cultural interests.
In this article, you will learn what social media warfare is and how you can best protect your organization from it.
20 years ago, scientists already predicted a “netwar “
This phenomenon was first described over 20 years ago. At that time, scientists predicted the development of a “netwar” in the 21st century. This, unlike cyber warfare, was not intended to focus on the attack of IT or communication systems. Rather, the aim of network warfare was to manipulate the perception of a specific group in a deliberate way and thus to damage the target of the attack. This concept is inherent in a specific approach to conflicts in the information age. In the digital age, blood no longer needs to be shed to eliminate a competitor and win a war, because information itself becomes the most powerful weapon that can be used by states, companies, small groups and individuals alike.
Social media as part of hybrid warfare
Today, this idea is no longer fiction, but rather reality. Various actors have understood and internalized the core concept of network warfare and increasingly rely on using manipulation tactics rather than physical attacks to push through their agenda. However, the concept of netwar has receded into the background. Now, this phenomenon is primarily located in the context of so-called hybrid warfare. Hybrid warfare is a military term that describes a mixture of different types of military and non-military warfare. Operations within the framework of hybrid warfare are usually carried out undercover and without an official declaration of war. Covert physical attacks or cyber-attacks as well as communicative and psychological tactics such as propaganda and disinformation are used. This approach, although it includes the fight by means of social media, does not focus on it. The situation is different with the concept of social media warfare.
What is social media warfare?
Social media warfare describes the use of social media as a kind of weapon with the aim of causing lasting damage to certain actors such as governments or companies. Various strategies and tactics as well as technological means are used in order to push through a political, economic, social or cultural agenda. Social media warfare is usually aimed at manipulating the perception and thus also the opinions, emotions and behavior of a specific target group, thereby harming the actual target of the attack. Examples of means in social media warfare include the dissemination of (false) information in social media networks, the use of social bots and the influencing of defined target groups by means of micro-targeting.
Social media warfare is thus also about a battle for attention, which is to be won by generating viral content and exploiting the mechanisms of the prevailing attention economy on the Internet. Thus, the attackers create narratives and content that are intended to emotionally address and polarize online users in order to stand out from the excess supply of content on the social web and achieve the greatest possible effect.
Who is involved in Social Media Warfare?
While the battle in social media was initially limited to the political arena, social media is now used by various actors as a strategic weapon. Thus, both as attackers and targets can be found in many areas of society. They can be roughly divided into four categories.
- Political actors: Political actors use social media to push through a certain political agenda. For example, social media warfare is intended to influence election results, destabilize political systems, or dismantle society’s trust in a government. Political actors include alliances of states, individual states, parties or even military units.
- Economic actors: In the economic sector, the motive of social media warfare is usually of a financial nature. Industrial groups or sectors want to assert their interests in order to gain an advantage or harm others. In addition, companies also use social media to discredit their competitors, to gain a competitive advantage and ultimately to assert themselves on the market.
- Actors with special interests: Besides political and economic ones, there are other motivations to participate in social media warfare. Lobby groups, for example, try to influence public opinion in order to obtain certain regulations and religious or political groups try to recruit more followers for their purposes.
- Actors with mixed interests: Ultimately, not all actors can always be assigned to a specific group, because some attackers pursue several goals at the same time or merely work on behalf of other actors. The group of hybrid actors includes exactly these attackers. One of the best-known examples of such an actor is the Internet Research Agency – a Russian company that has been involved in various information operations in the past to enforce the interests of both the Russian government and individual Russian companies.
All in all, social media warfare is nowadays accessible to everyone without much effort, because little technical know-how and Internet access are enough to launch a digital attack in social media. Thus, individual users on the social web can quickly and easily gather comprehensive information about an attack target, share manipulative content with a target group and use micro-targeting and paid ads to play it out even more specifically, or contact a target group directly via private messages, discuss it with them and convince them of a particular matter.
Social media warfare as a threat to companies?
Companies can quickly get caught in the digital crossfire of a social media attack. Large companies and corporations are particularly at risk, as they are increasingly in the public eye and are particularly vulnerable to slander campaigns. In addition, large companies and corporations usually offer a greater scope for attack, as they often take greater account of socially relevant topics such as social responsibility or corporate digital responsibility than smaller companies. A possible or alleged misconduct thus attracts the attention of a broad mass of people more quickly, triggers outrage and opens up points of attack that are exploited by competitors or interest groups.
At the same time, competitors and attackers can also use social media to cause damage to a company without directly attacking it. For example, competitors can use the unfair means of social media warfare to strengthen their own position in the market or industry groups or lobbying associations can massively influence the business conditions for companies. Ultimately, the manipulation of society’s perception of issues can also lead to the enforcement of certain regulatory conditions and thus cause massive damage to entire industries.
What are the strategies and means in social media warfare?
In the context of social media warfare, social media can be used in different ways and with different strategic orientations. If social media is used to attack companies, institutions or individuals, one generally speaks of offensive strategies. In the end, the attackers always intend to damage the target in one way or another. They can be represented by four categories:
Targeting and Information Gathering
In targeting, social media is used to identify potential targets for attack. In a military context, for example, this means locating enemy troops by investigating the social media behavior of the members of the troops (e.g. by means of geo-tagging) or by gaining access to social media accounts. If we look at targeting in the context of corporate attacks, one of the aims is to identify individual targets within an organization – who, for example, is the CEO of the company and how could his social media behavior be used for an attack? This aspect is closely linked to the possibility of using social networks to gather as much information as possible about the target and the stakeholders of the target.
If, for example, the opinion of a certain group (customers, business partners, etc.) is to be manipulated, social media profiles are first identified and analyzed. The information then helps to design precisely tailored tactics and content in order to manipulate this group as effectively as possible. In addition, the misconduct of individual stakeholders such as business partners or suppliers can also be instrumentalized to damage the reputation of the stakeholder and thus also the reputation of the actual target of the attack. This procedure is also known as Discreditation by Proxy.
Manipulation through information
The manipulation of entire societies or individual stakeholders is a central strategy in social media warfare. For example, the opinion, values, emotions and thinking of a specific target group are to be influenced in such a way that consequential effects are created that damage the actual target of the attack. For instance, the use of digital propaganda is supposed to influence election results or induce customers to stop buying from a certain company. To achieve this goal, attackers can pursue different approaches:
- Deception: By spreading false information or rumours, attackers try to deceive their target group in a systematic way. It is also common to produce artificial attention for one topic in order to divert attention away from another.
- Confusion: By providing contradictory information, attackers try to create confusion and a feeling of insecurity in the target group. This makes the target group more prone to simplifying representations and propaganda designed to harm the target.
- Division: The attackers try to divide societies or groups by spreading extreme opinions as well as hatred and agitation on the Internet. The public conflict, in turn, is supposed to lead to strong negative feelings and a higher susceptibility to certain narratives.
- Exposure: The attackers publish (false) confidential information or data in order to publicly expose the target of the attack.
- Discrediting and defamation: The aggressors attack the reputation of the target and spread reputation-damaging and defamatory content in the social media.
Regardless of the target and the approach the attackers pursue, the possibilities of using information as a weapon in social media warfare are vast: So-called open methods are, for example, the distribution of rumors, false or confidential information and other content via official social media accounts of influencers and opinion leaders such as politicians, celebrities or employees of a company. By this kind of distribution of polarizing content, disinformation or accusations, the attackers can quickly reach a wide audience, trigger a flame war and even draw attention to traditional media. In addition, ‘real’ influencers usually have a great influence on the opinion of a target group because they enjoy a high degree of credibility.
Fake identities, sock puppet accounts and social bots
If the attackers proceed covertly, they usually create fake identities in social media – so-called sock puppet accounts – or hire Internet trolls to distribute polarizing content. This content ranges from individual negative comments and ratings to large-scale digital character assassination campaigns and the targeted addressing of individual users via paid posts and advertisements in order to influence their opinions in one direction or another.
So-called social bots and bot networks are also a popular means of influencing opinion. They can achieve an enormous reach for content within a very short time, because bots post, link, comment or share automatically and every second, thus artificially amplifying the reach of the content. Bots can also be used for the purpose of classic spamming to create a kind of “information overload” for a specific target group on the Social Web. The result: the target group is confronted so often and regularly with a narrative, a rumor or certain information that a habituation and memory effect sets in and the target group begins to believe the content (the so-called mere-exposure effect).
Hashtag hijacking
In order to continue to distribute one’s own content and messages with the greatest possible reach, the so-called hashtag hijacking is still used. Here, the attackers “hijack” already existing and above all very well-known, trending hashtags and post their own content among them with enormous firepower and frequency. The result: the actual content of the hashtag is suppressed and users searching for the hashtags are mostly confronted with the manipulating content of the attackers.
Mobilization and commitment
In addition to influencing perception, thinking and emotions, social media warfare is also about the manipulation of behavior – even outside the social web. It not only tries to influence what people like, share or comment on, but also how they behave far away from the digital world. The digital attackers, for example, try to persuade a particular target group to get involved in a campaign against the actual target and, for example, to call for protest against political plans or boycott companies or products.
The swarming tactic
To do this, the adversaries resort to a kind of swarming tactic: with the help of unfair means such as bots, they give the appearance of an angry digital mass and try to infect real users with their anger and indignation. The result: real users become part of the online mob and in turn mobilize more and more other (real) users. The result can be a (fake) protest or a (fake) boycott, which would never have happened without the intervention of the attackers. At this point the attackers also make use of so-called astroturfing. Astroturfing uses communicative measures to fake already existing protest or “grassroots movements” – always with the aim that real people can join this fake movement and thus enforce a certain agenda.
Social engineering
Another means of manipulating behavior is so-called social engineering. This is an attempt to use psychological manipulation to persuade the targets to take certain actions, such as the disclosure of confidential information and data. Social Engineering became known in 2010 by IT expert Thomas Ryan, among others. Ryan had created the virtual art figure Robin Sage, created a profile for her in social networks and used it to contact politicians and company bosses in order to extract confidential information from them – and with great success. This process, in which (fake) people feign a relationship with an attack target in order to get information, data or even pictures of the person that are not completely G-rated, is also known as honey trapping.
Social Cyber Attacks
A special category of social media warfare is the combination of classic cyber-attacks and manipulation methods in the social web, the so-called Social Cyber Attacks. Classic cyber criminals are also making an increasing use of social media and are trying to send malware and malicious software via public posts of fake accounts or direct messages in the messenger applications of the networks or to gain access to important data with the help of social engineering.
In addition, social media accounts are increasingly becoming a target for hackers to access information (e.g. from private conversations) via the profiles or to share content via the hacked profiles. On the other hand, the warriors in social media warfare are also resorting to classic cyberwar methods such as hacking, for example, to gain access to data and information that is then to be distributed via social media with a wide reach. There are signs of an increase in such hybrid attacks, for which companies in particular should be prepared.
Finally, one thing needs to be made clear: The methods listed here are only examples, because in social media warfare there is an unlimited selection of strategies and means, the number and sophistication of which is constantly increasing with the ongoing technological development. Only those who are familiar with the existing methods of attack and always keep up to date with the latest technology can protect themselves from becoming part of social media warfare and know what to do in case of an emergency.
How to manage the danger of social media warfare?
The protection against and defense of attacks in or through the social web is becoming more and more complicated. Meanwhile, there are no longer just a handful of social networks, but a multitude of social networks where attacks can be carried out. Added to this is the problem of so-called dark social applications – apps whose traffic cannot be tracked (these include messengers such as WhatApp or Telegram). These too are increasingly becoming the playing field in social media warfare. The consequence: effective monitoring is hardly possible without comprehensive expertise and knowledge of these problems, which enormously reduces the ability of institutions, companies or individuals to act in the event of an attack.
Preparing countermeasures
Anyone who becomes the victim of an attack then quickly falls into a passive reaction mode, which is characterized by the fact that it is necessary to gain an overview of the platforms, strategies and tactics of the attackers and possible countermeasures – and these can change again and again in a very short time. In order to best prevent such an inability to act in an emergency, it is essential to raise awareness of the topic, to incorporate the danger of “social media warfare” into one’s own risk management and to prepare defensive counter-strategies for the emergency.
Empowering employees
In addition, empowering your staff is of central importance. Employees must know how to recognize attacks via social media at an early stage and defend against them adequately. This is not just a matter of theoretical knowledge, but of real experience. Our immersive simulation trainings provide exactly this experience and prepare you and your team practically for defending against social media warfare. Our information warfare simulation is specifically designed for this purpose.
Better be safe than sorry.
Download infographic
More interesting insights
-
The outrage economy of social media
Read more -
What is disinformation?
Read more -
Social Media Crisis Communication: Social Media Care & Speed Factor
Read more -
How Fake Reviews Threaten Your Reputation and What You Can Do About It
Read more -
Digital risks and cybercrime – developments and trends in 2021
Read more -
Cancel culture and reputational crisis
Read more -
Dealing with Covid-19 Conspiracy Theories in the Office
Read more -
5 tips for using chatbots in crisis communication
Read more -
What is reputation risk management?
Read more -
Crisis management training: Are you ready for an emergency?
Read more